Tamper Security is a security feature implemented in the 1903 version of Windows 10, otherwise referred to as the May 2019 update. Tamper Protection prevents the altering of Windows Security and Windows Defender settings by applications, Windows command line tools, registry updates, or team policies. Users must instead switch security settings directly through the Windows 10 user interface or through Microsoft business software like Intune. If Tamper Protection on your Windows 10 device isn’t currently enabled, Microsoft has told that all Windows 10 users would implement this change. It may take a few days, however, before it is automatically available for everyone. You can now allow it if you don’t want to wait by following these instructions.
Tamper protection is an important tool for preventing bypasses of security
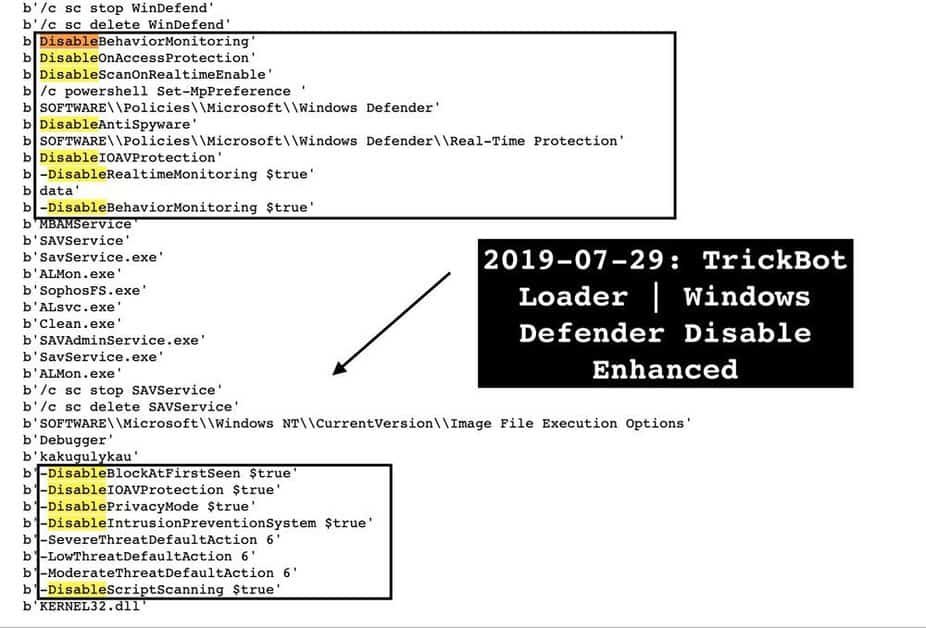
Despite Windows Defender being introduced to Windows 10 and becoming a robust anti-virus tool, malware has made a growing attempt to circumvent it. This is achieved by trying to disable or limit Windows Defender features using PowerShell commands, team policies or registry modifications. For example, we saw the TrickBot, GootKit and Nodersok trojans made a concerted effort over the course of the last 4 months to circumvent Windows Defender to live on an infected computer or to bypass its protections.
TrickBot disabling Windows Defender protections However, these attempts to change Windows Defender or Windows Security settings are ignored or reset with Tamper Protection allowed. Because Windows Defender automatically allows Tamper Protection by disabling any third-party antivirus software, it is even more critical that the Windows Defender is able to properly protect you.
Consumers use the settings for Windows Security
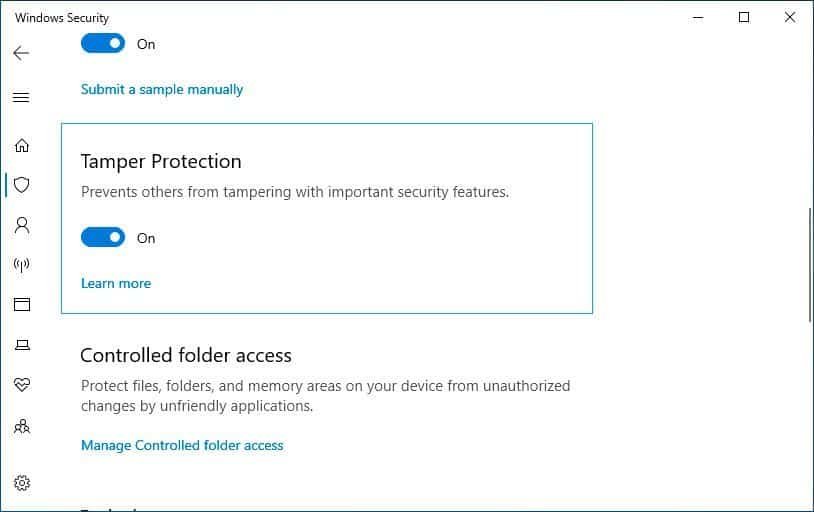
For users, Tamper Defense is handled in Windows Security under Virus & Risk Protection. You can do this by opening Windows 10 settings, clicking Windows Security, then Virus & Risk Protection, and then clicking Manage Virus and Threat Protection Settings. Download and you will see an option called Tamper Protection that should be disabled as shown below.
Managing Tamper Protection in Windows Security
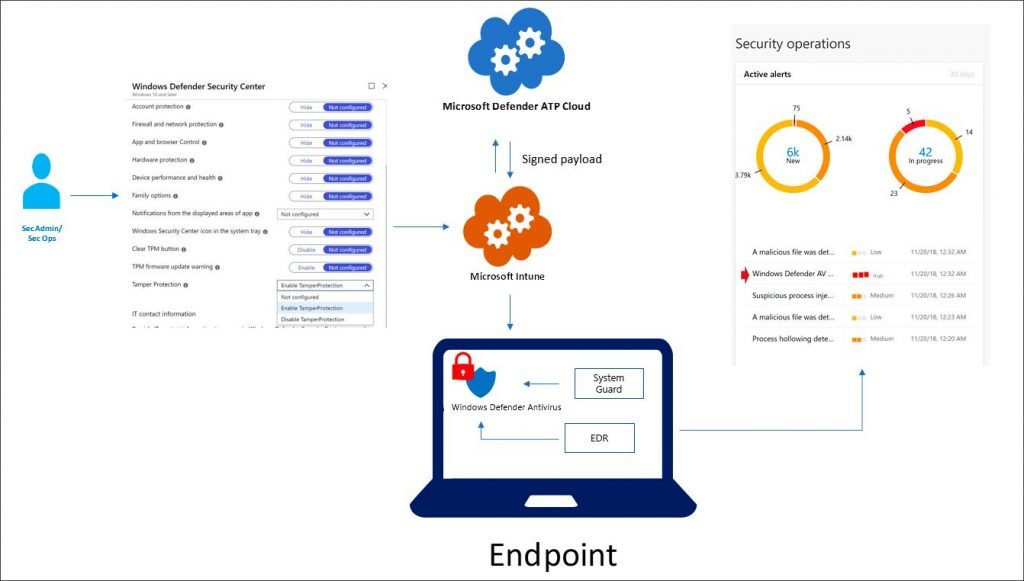
Organizations use Intune to control the security of manipulators
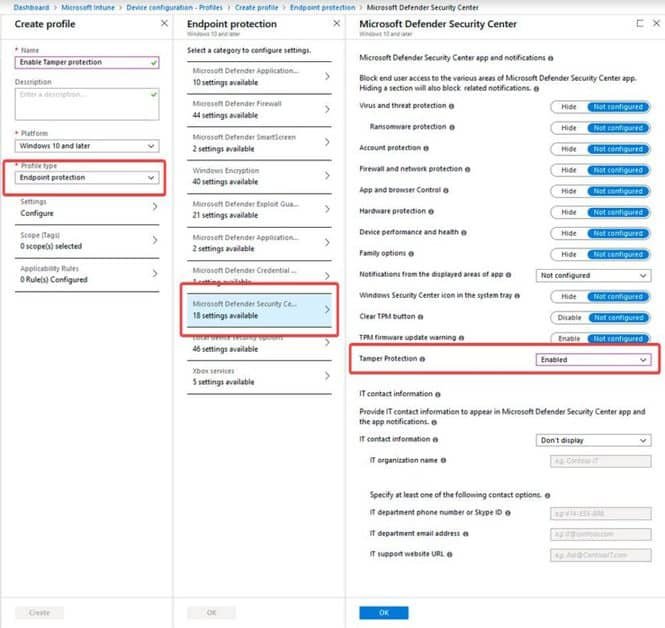
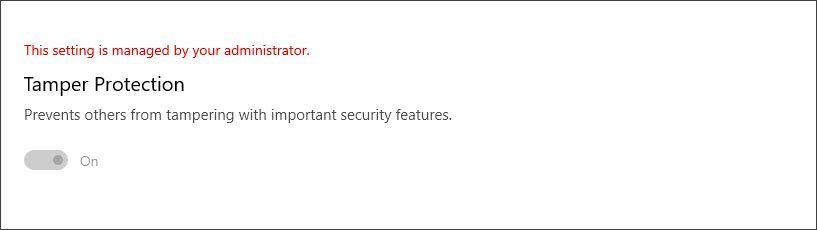
Although Enterprise workstations can require Tamper Protection with the same method as customers, managers can also use Microsoft Intune management software to manage it. Intune allows Tamper to secure the entire org, device types, or even user groups, as shown below. Managing Tamper Protection in Intune When enabled via Enterprise software, workstations show that your “administrator manages” this setting. Managed by Admin To provide additional security for Tamper Protection Management, Intune must digitally sign the request each time adjustments are made to the Tamper Protection settings. If this request is received by a workstation, it will confirm that the signature is legitimate and if not, ignore the changes. You can see an example of how Intune sends such signed requests out below.
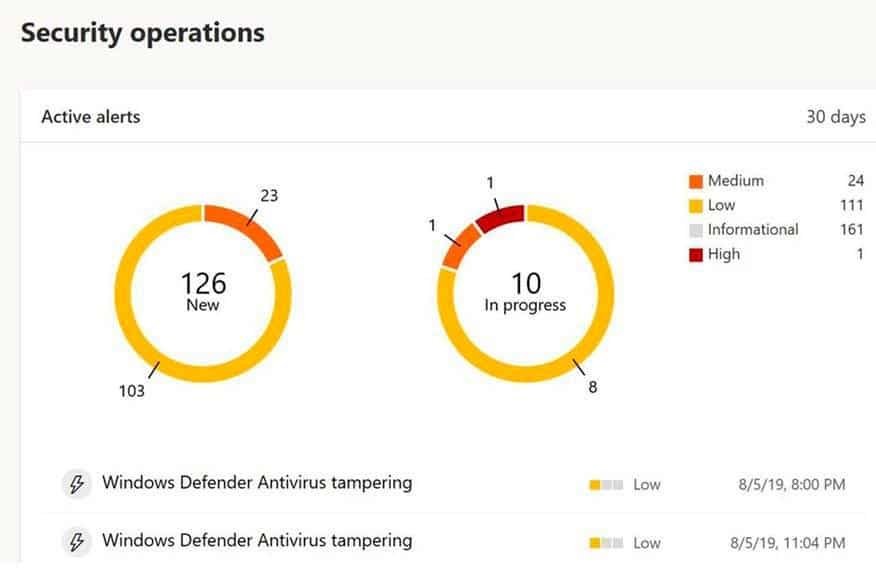
Microsoft Intune Signed Message If an attacker tries to tamper with Windows Security or Windows Defender settings, whether malware or a local user, a warning will be pushed to the Microsoft Defender Security Center. Administrators can then view these warnings to see which device is being abused and remediation is undertaken.
Tamper Protection Alerts in Microsoft Defender Security Center This functionality is not only critical with malware actively aimed at Tamper Protection, it must be able to provide complete protection to Windows 10 users. Both users must ensure that Tamper Protection is allowed, whether customers or business organisations.