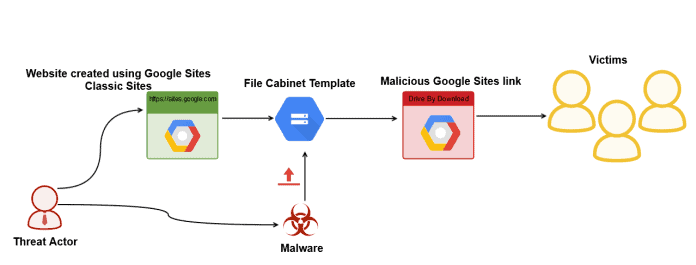
Threaten actors abuse the Google file cabinet template and use it as an exfiltration medium and SQL to share the stolen data to the remote server. Google Sites allows anyone to create simple websites that support collaboration between different publishers. You can create a place to “store” documents, images, pdfs, presentations or any digital file with the template file cabinet. Since the malware is supplied by the trusted provider, the attack’s infection ratio would be extremely high. Other Google services such as Gmail block malicious uploads, but the template for Google file cabinets does not block any malicious files and protect them from being uploaded.
In this case, researchers discovered this banking trojan as Win32.LoadPCBanker.Gen and the malware being delivered from the following Google Sites URL:https://sites.google[.]com/site/detailsreservations/Reserva-Manoel_pdf.rar?attredirects=0&d=1. Google Websites Hosted with Malware Threat actors who use Google’s ‘ Recent Site Activity ‘ option containing a malicious file attachment with the name “Reserva Manoel.” Attackers using classic Google sites are using the malware upload template for creating a website and generating malicious URL that are shared with target victims.
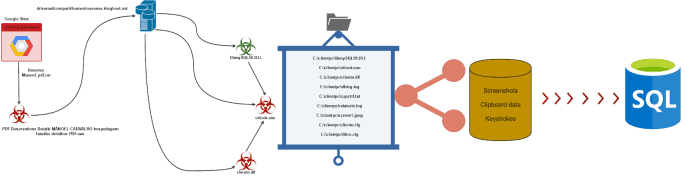
Delivery mechanism of the malware using Google sites The malicious URL hosting the LoadPCBanker malware on Google’s websites drops the first step parent downloader after the execution process. Firs Stage of downloader later drops the next stage payloads from a file hosting website. According to netskope analysis, RAR archive “Reserva-Manoel_pdf.rar” contained an executable ”PDF Reservations Details MANOEL CARVALHO hospedagem familiar detalhes PDF.exe”. The filename translates to “PDF Reservations Details MANOEL CARVALHO guest house details PDF.exe” from Portuguese to English, indicating to be likely targeting Brazil or Portuguese speaking users. The next-stage payload is Otlook.exe and cliente.dll, and libmySQL50.DL is a mysql library used in the server transmission of victims data.
Attack Kill chain of LoadPCBanker In addition, the next step payloads collect screenshots, clipboard data and the victim’s keystrokes. Finally, Netscape says it uses SQL, an exfiltration channel to send victim data to the server.