The new WiFi hack, discovered by the lead developer of the popular Hashcat password cracking tool, Jens’ Atom’ Steube, explicitly works against WPA / WPA2 wireless network protocols with enabled roaming features based on the Pairwise Master Key Identifier (PMKID). Steube accidentally discovered the attack to compromise the WPA / WPA2 enabled WiFi networks while analyzing the newly-launched WPA3 security standard. This new WiFi hacking method could allow attackers to retrieve pre-shared key (PSK) login passwords, allowing them to hack into your WiFi network and communicate with the Internet.
How to Hack WiFi Password Using PMKID
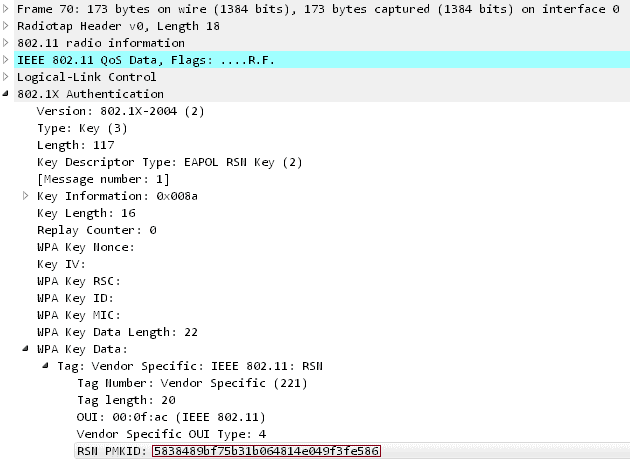
According to the researcher, attackers must wait for someone to log into a network and capture a full 4-way authentication handshake of EAPOL, a network port authentication protocol, according to previously known wifi hacking methods. The new attack does not require another user to capture credentials on the target network. Instead, it is carried out using a single EAPOL (Extensible Authentication Protocol over LAN) frame on the RSN IE (Robust Security Network Information Element) after requesting it from the access point. The Robust Security Network is a protocol for secure communication over an 802.11 wireless network. One of its capabilities is PMKID, the key to connecting a client to an access point. Step 1- An attacker can use a tool, such as hcxdumptool (v4.2.0 or above) to request the PMKID from the target access point and dump the received frame into a file. $ ./hcxdumptool -o test.pcapng -i wlp39s0f3u4u5 –enable_status Step 2- The frame output (in pcapng format) can then be converted to a Hashcat- accepted hash format using the hcxpcaptool tool. $ ./hcxpcaptool -z test.16800 test.pcapng Step 3- To get the WPA PSK (Pre-Shared Key) password, use Hashcat (v4.2.0 or higher) password cracking tool, and bingo, that’s how to hack the wifi password. $ ./hashcat -m 16800 test.16800 -a 3 -w 3 ‘?l?l?l?l?l?lt!’ This is the wireless network’s password, which can take time depending on its length and complexity. “We don’t know which vendors or how many routers this technique will work for at this time, but we think it will work against all 802.11i / p / q / r networks with enabled roaming functions (most modern routers),” said Steube. Since the new wifi hack only works on networks with enabled roaming functions and requires attackers to force brute passwords, it is recommended that users protect their wifi network with a secure password that is difficult to crack. This wifi hack also does not work against the WPA3 wireless security protocol of the next generation, since the new protocol “is much harder to attack due to its modern key establishment protocol called” Simultaneous Authentication of Equals “(SAE).” Disclaimer: Please be aware that WPA / WPA2 is illegal unless you have permission from the network owner and the parties involved. This post should be used to help the public understand how hackers gain access to your wifi passwords ( although designed as a safety tool). The CybersGuards team shall not be held responsible if any criminal charges are brought against any person who misuses the information on this website to violate the law.